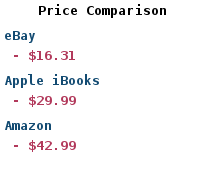Mastering Metasploit
Write and implement sophisticated attack vectors in Metasploit using a completely hands-on approach

Book Description
The Metasploit framework has been around for a number of years and is one of the most widely used tools for carrying out penetration testing on various services.This book is a hands-on guide to penetration testing using Metasploit and covers its complete development. It will help you clearly understand the creation process of various exploits and modules and develop approaches to writing custom functionalities into the Metasploit framework.
This book covers a number of techniques and methodologies that will help you learn and master the Metasploit framework.
Book Details | |
| Publisher: | Packt Publishing |
| By: | Nipun Jaswal |
| ISBN-13: | 9781782162223 |
| ISBN-10: | 1782162224 |
| Year: | 2014 |
| Pages: | 378 |
| Language: | English |
Book Preview | |
| Online | Mastering Metasploit |
Paper Book | |
| Buy: | Mastering Metasploit |